Summary
Kaspersky 2018 Q2 Threat statistics have been released. Kaspersky has reported the workings of Operations Parliament a cyber-espionage campaign aimed at high-profile legislative, executive and judicial organizations around the world. These attackers target, parliaments, senates, top state offices and officials, political science scholars, military and intelligence agencies, ministries, media outlets, research centres, election commissions, Olympic organizations, large trading companies and others. Major African countries affected were:
- Djibouti
- Somalia
- Egypt
- Morocco
These group installs malware that provides remotes access to the victim’s computers, where they can execute commands and exfiltrate data.
Use of Phishing
Kaspersky also reports a hacking group known as Crouching Yeti (aka Energetic Bear) an Advanced Persistent Threat (APT) that has been active from 2010 targeting Industrial control systems (ICS) but target has been in Europe and the US. The group use phishing emails with malicious attachments which would infect the victims. These group use publicly available vulnerabilities hence the need for continuous patching.
Mobile Malware
Kaspersky reports ZooPark a cyber-espionage group that targets Android devices. This group installs malware on mobile phones that are able to collect call logs, audio recordings of calls, GPS location, browsing data, photos etc. At times these malicious actors, hijack popular news sites where users are misdirected to sites where they download this malware.
Internet Explorer Vulnerability
Despite the fact that Microsoft has moved on to the Edge browser, attacks are being noted on the older internet explorer, which even though Microsoft has fixed vulnerabilities attacks are noticing that start with a malicious Macro embedded Word document.
Infected Routers
A malware known as VPNFilter was able to infect various brands of routers. The affected routers included Linksys, MikroTik, Netgear, TP-Link, ASUS, D-Link, Huawei, Ubiquiti, UPVEL and ZTE. While the FBI was able to limit the damage of this malware, by sink-holing one of the domains it is still unknown who was responsible for this malware.
Insecure Mobile apps
In a review of 13 Million mobile apps, Kaspersky noted most of them were not encrypting communication to various third-party servers. This meant they were leaking various sensitive information such as IMEI, IMSI, Manufacturer and model of the phone, age, phone number, name, emails and so on.
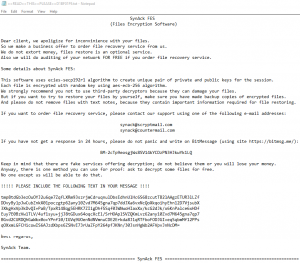
Ransomware Rules
Ransomware malware continues to grow albeit this time more targeted, unlike the Wannacry version that targeted the world en-masse. By being specific, the ransom demands have also gone up even as high as $3,000
World Cup Fraud
Before the world cup kicked off, the Cybercriminals had already created phishing emails, and fake websites with FIFA world cup themes such us notifications of fake lottery wins to lure the unsuspecting individuals to provide their credentials such as name, address, e-mail address, and telephone number.
You can read the entire report here
For any Cybersecurity issue, you can always contact us.